Unfortunately for many computer users who are not necessarily IT geeks or security minded people, the antivirus is like Zeus, the almighty protector in which they put all their trust. (if you search for the keyword ‘security’ in torrent portals, you’ll notice that the most downloaded items by far are antivirus tools)
You may ask why? Well, in my opinion there are a couple of reasons, but the main ones are the following:
- Excellent marketing based on people’s fear from AV vendors
- Lack of information security knowledge due to poor or nonexistent education about the internet and the online threats in the school systems
- Constant growth of malware and hacking activities
In fact little do people know that installing an antivirus does not always clean viruses or prevent them from infecting their computers, sometimes it can even be the opposite: they can expose you to more risks and threats. Think about it this way: if it rains lightly outside, you put your raincoat on and you’re safe, but if a storm suddenly starts, your raincoat becomes useless. This is how antivirus software is. The security of a system is achieved by thorough hardening of various components while the AV is just one piece of this process.
But imagine the raincoat has holes in it to begin with. Yes, even antiviruses can have security vulnerabilities that can be exploited to infect your computer, steal your private data or use your machine as a bot in some cyber bank robbery.
Actually, the reason I wrote this article is because I wanted to share a little story about my experience with a well-known antivirus called BitDefender.
I had some free time during the weekend, so I decided to install it to add more security to my fresh OS. I was mainly looking to test the “dual-firewall” feature which allows you to block or allow network connections made by processes in real time. I chose BitDefender because it had good reviews, a proprietary detection engine but also because it is known as one of the best home-use antiviruses on the market.
Unfortunately I ended up discovering several security bad practices that made me uninstall the product after ~2 hours. I want to discuss them below so people and companies become aware of these risks and take them into account when assessing any AV solution they wish to purchase.
So let’s start off:
When I installed the trial version it requested me to create an online user account (I imagined for license management mainly). After I finished the installation I noticed this online account was synced/integrated with my endpoint protection agent. There seemed to be no apparent way to log the account out of the AV dashboard, unless you log in with another account (1st issue)
I started poking around the settings to “harden” the antivirus, yes, you need to do that as well :). While going through the settings I noticed issue number (2), apparently updates are downloaded via a plain text connection (which means that hackers sitting in the same network with your computer can perform man in the middle attacks and push tampered signatures as updates to avoid real viruses from being detected or can actually try to fuzz the antivirus to find application vulnerabilities in its updating mechanism). At this point I was a little bit unhappy about the security impression that it gave me, but I continued to analyze its other characteristics.
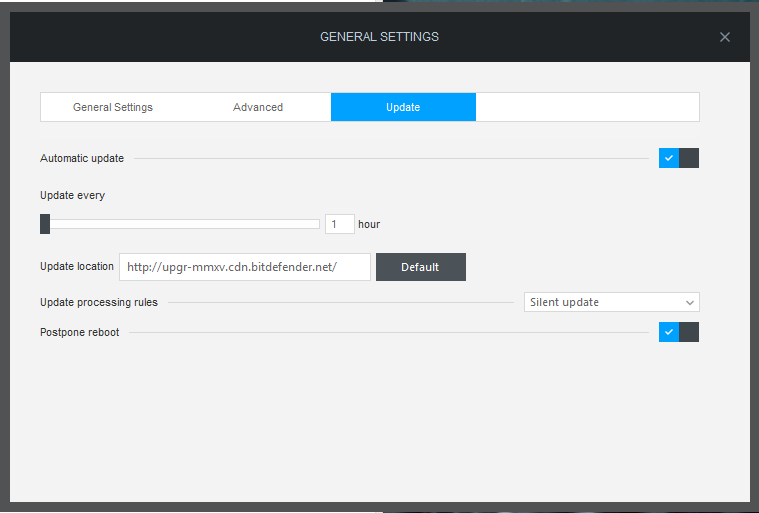
Next thing I did was to log onto my online account at my.bitdefender.com. Obviously I forgotten my password so while using the recover password module I found out the next issue, which is that you can actually enumerate valid account by their email addresses thanks to the error message returned. (3)
I continued to log in after I successfully set a new password to discover a couple of interesting aspects:
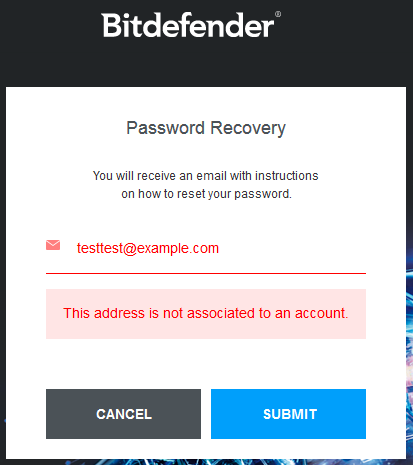
The online dashboard was having some rather complex capabilities: to start with, it was having my computer’s hostname and domain listed, it had remote scanning and reporting capabilities (basically I could scan my computer remotely from that account, given the computer had an internet connection, and see the results in the dashboard), other features were: locate my device, remote lock and system wipe.
As an ethical hacker I immediately started to acknowledge the risks: anyone that manages to get access to this online account can potentially lock me out of my computer, wipe my system remotely or find out where my laptop is. Additionally, he could perform remote scans, maybe to impact my system’s performance or verify if a delivered payload is being blocked by the AV or is blocked by an IPS or a firewall.
So then I fired up a local proxy to see what type of data was my account sending to BitDefender servers and what type of data was BitDefender receiving from the agent. I also wanted to analyze the authentication security controls to make sure that at a minimum, best practices are followed and I can safely use the software.
Unfortunately this only lead to the discovery of even more bad practices:
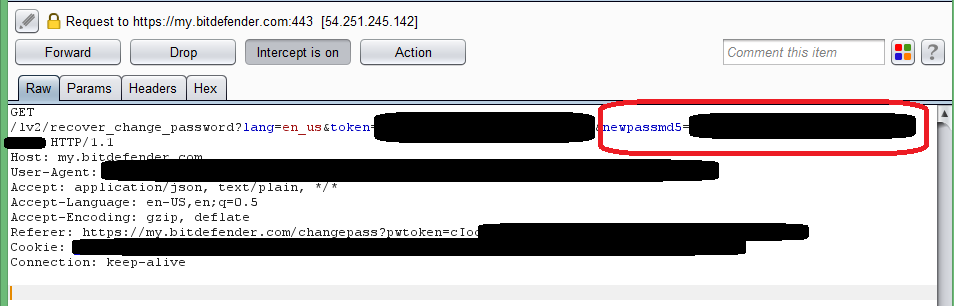
- Username, password and session token were sent in clear text as GET request parameters, effectively ending up being stored in server access logs available to any server admin to play with and obviously in my browser’s history
- The password recovery process worked in a such a manner that I’m assuming they store passwords as MD5 hashes in the database, which is obviously broken and prone to collisions
3. I noticed my currently logged in local administrator username was being sent by the agent to BitDefender and retrieved in a JSON object by the online dashboard, I didn’t understand why as it was not being displayed anywhere
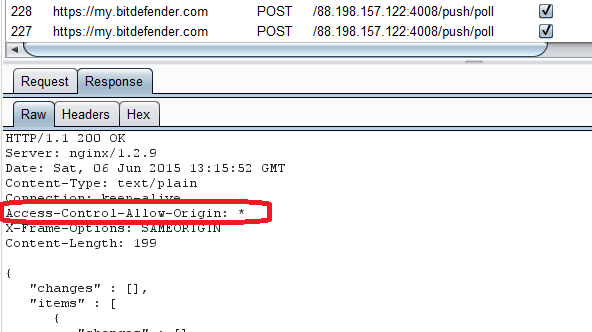
4. Universal allow in the Access-Control-Allow-Origin header, this is a common mistake when dealing with COR, it could potentially allow for CSRF vulnerabilities to be stealthily exploited or it can allow hackers to write Javascript that tricks other users to exploit vulnerabilities found in BitDefender’s web platform.
5. I tried to “bruteforce” my own account, basically I tried to log in with an invalid password and see what will happen, and noticed the account is only getting blocked for a couple of minutes after few invalid tries then it gets automatically unlocked (didn’t see any captcha anywhere). Don’t you think remote wipe or remote lock would be funny attack vectors when targeting users that decide to link their Facebook account with BitDefender or to set “123456” as their password for the AV account?
6. At this point I decided to uninstall the antivirus, only to notice that after uninstall, my online account was still accessible and it still had my device and all its details (hostname, domain, local admin user, GPS location, my home WiFi’s SSID and mac address etc.)
7. Trying to remove the device was not working and I couldn’t find a way to close the account 🙁
All these bad practices prove that sometimes even security software that is designed to keep you protected can expose you to more risks. This little story resulted from just 2 hours of analyzing, not testing the security of the product. This shows once more that only by having a holistic security approach in which you perform threat modelling, app testing, security unit testing, code reviews etc. you can build secure products.
I like to conclude that AV software should not be perceived as the perfect health pill. Sometimes you take pills to resolve a health issue and you end up having a different one. So the AV is no Zeus to the computer, it is not protecting us from all evil but in fact it can sometimes open doors to a different kind of evil.
PS: I only performed passive analysis and did not perform ethical hacking or penetration testing on any of BitDefender’s software. I also did not assess its virus scanning engine.
by Tudor Enache
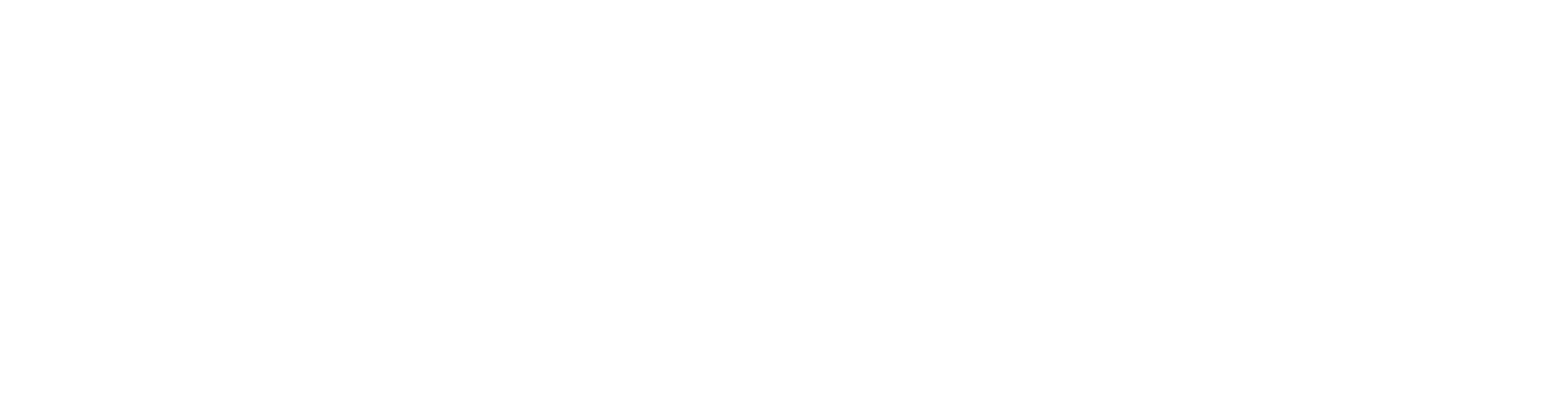

28,893 Comments
Hassan
1. Did you report this to vendor? 2. If yes then what was the response?
offensivebits
no we didn’t report it!