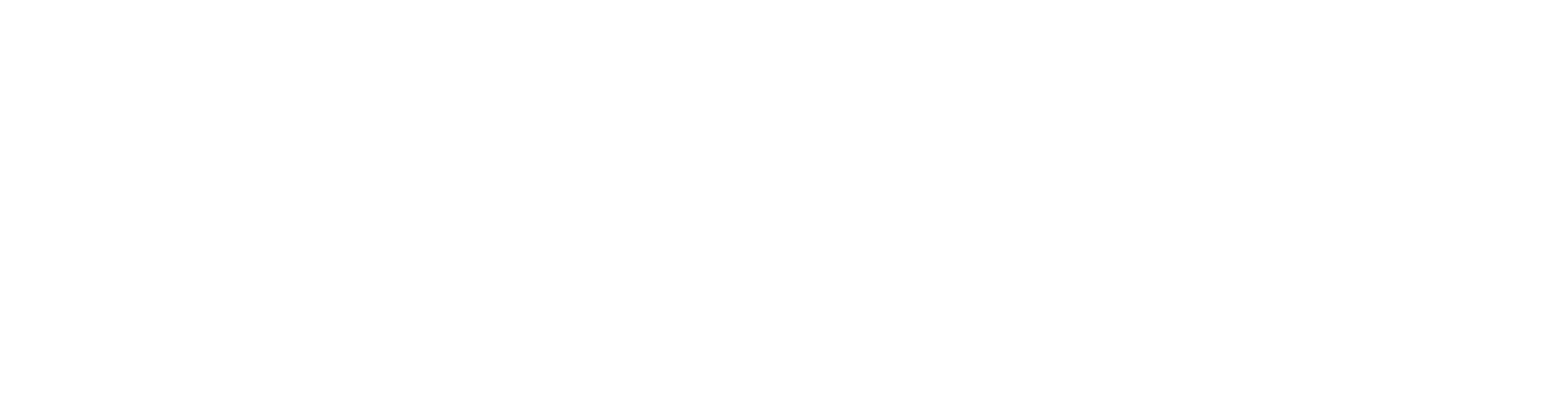On 5 June 2012, the social networking website LinkedIn was hacked and Russian Cybercriminals stole passwords for nearly 6.5 million user accounts. The website repeatedly encouraged its users to change their passwords after the incident and Vicente Silveira, the director of LinkedIn, confirmed, on behalf of the company, that the website was hacked in its official blog.
Most of stolen passwords were successfully cracked and posted on Russian password forum later on that day.
Offensivebits team found more than 45 thousand accounts belonging to UAE governmental and private entities
Consequences of the breach
Hackers may use all of cracked passwords to log into other online services such as (gmail,office,etc). The wordlist of cracked passwords are now available on different cracking websites, which make it much easier for hackers to brute-force your account using this leaked wordlist.
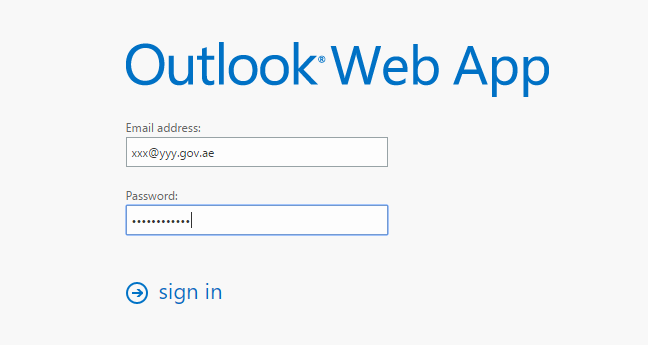
For example, if one of the compromised accounts was [email protected], hackers can visit http://yyy.gov.ae and fine the Web Mail Page and try to login using the leaked credentials.
Recommendations
- It is not recommended to use corporate email for social network registrations.
- Use different password for every online service.
- Its recommended to enable OTP or 2FA on your online accounts.
- Ensure that strong password policy is applied on your online accounts.
- We also advice organizations to use the following service https://haveibeenpwned.com/DomainSearch to check the accounts that are compromised and to reset the passwords if they are using them for in any other public services